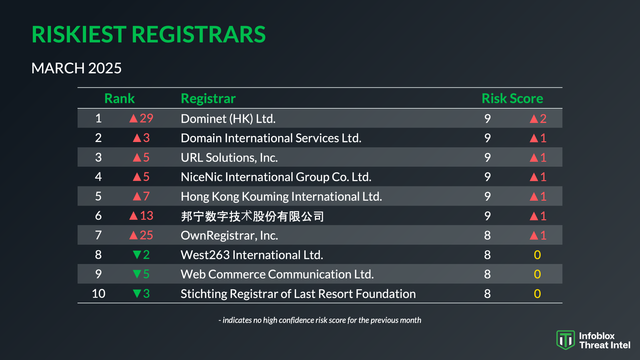
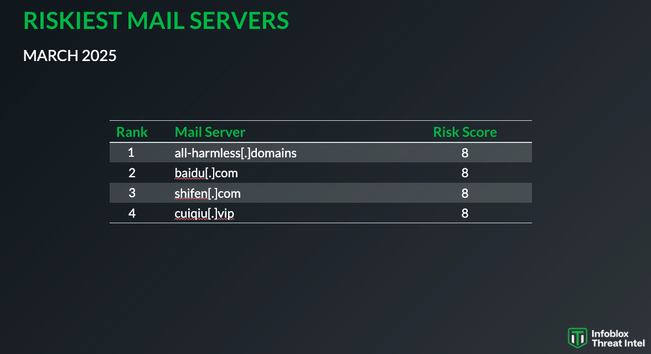
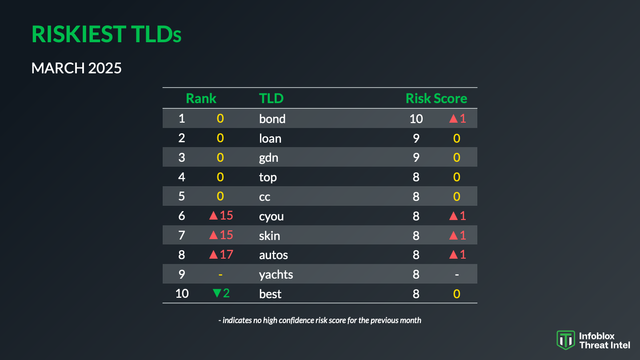
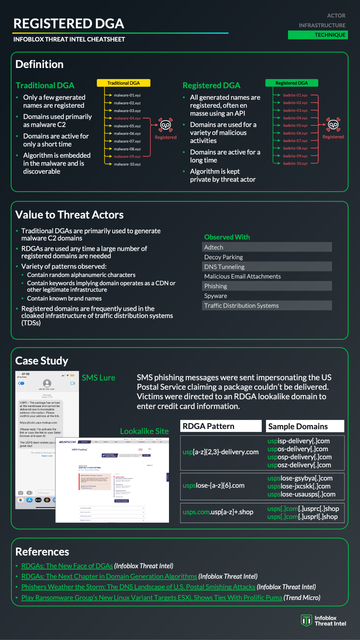
The hack that turned the US government website of the Center for Disease Control into a porn site turns out to be more interesting than I originally thought. And that's not just because the CDC has not done anything to fix the problem 24 hours later...
Yesterday we found that a number of universities, enterprises and other government sites have been hacked by the same actor. Visiting the specific URLs takes you into a malicious adtech traffic distribution system (TDS). Depending on your device and location, you might get the pornography. bud, you also might get other scams like scareware. From my sacrificial phone, I was able to trigger a bunch of push notification requests.
Bottom Line: malicious adtech pays, their TDS allow actors to hide, and hackers are quite happy to compromise well known websites to get that money. But it's not just about scams, these types of techniques are frequently used for delivering information stealers, which lead to breaches.
Here's a few notes about the attack:
* The site is modified to add pages which attempt to load a specific image name. If that isn't there, then it redirects to the actor controlled malicious domain which funnels into the TDS
* The actor seems to be using blogspot for this now, but previously used a tiny URL. From here they will go to adtech TDS.
* There were what seemed possible to be dangling CNAME records in many cases, but in some of them didn't appear to be any issues with the DNS records. I suspect combo of accesses.
* In cases where there's no apparent DNS record issue, the legit site seems to be hosting in GitHub. Perhaps they have a credential compromised.
* I saw at least two adtech companies used, Adsterra and Roller Ads. these are checking for VPN and anonymous proxies before serving the final landing page.
* This image redirect actor seems to be riding off of a different actor who originally hacked the site, uses SEO poisoning techniques, and hacked universities to host porn content.
I put a bunch of images in imgur.
Thanks Krebs for the lead.
#dns #cybercrime #cybersecurity #infosec #adtech #malware #scam #threatintel #tds #InfobloxThreatIntel
https://imgur.com/a/cdc-website-hijack-leads-to-malicious-adtech-XfguIcN